Note: |
To make UEFI systems with Secure Boot work with the pre-built veeamsnap kernel module, you need to enroll the Veeam public key to the MOK list using the mokutil utility. The key is available in the veeamsnap-ueficert-4.0.1.XXXX-1.noarch package residing on the Veeam repository. To enroll the key:
|
To install Veeam Agent for Linux:
For CentOS 7, ensure that the system has the correct Linux kernel sources from the CentOS repositories: $ sudo yum install -y kernel-devel-$(uname -r) kernel-headers-$(uname -r) Update the repository cache and install the driver using the nvidia-driver-latest-dkms meta-package. Turn on and install EPEL Repo on a CentOS 7.x You must install dkms for registering the NVIDA kernel module with DKMS: $ sudo yum -y install epel-release $ sudo yum -y install dkms. I am running now NVIDIA card, simply dont install dkms if that is the case, you will still get the driver regardless But if you are desperate, check the headers match your kernel version. Sometimes, when the header is not install along with your kernel, then you do install it at latter time, the system will offer a header that is not match with.
- Download the Veeam software repository installation package (veeam-release) from the Veeam Download page, and save the downloaded package on the computer where you plan to install the product.
Tip: |
If the computer where you want to install Veeam Agent for Linux is not connected to the internet, you can download and install Veeam Agent for Linux packages manually. To learn more, see Installing Veeam Agent for Linux in Offline Mode. 6.5 grendel load data for a-bolt action. This was modified for European competition, being necked down to form the 220 Russian. The 6.5 Grendel provides an extreme range capability for hunting, competition and tactical applications. The 6.5 Grendel has the flexibility to move from lightweight varmint bullets in the 90-grain class, which offer superb accuracy for competition and small game shooting, to mid-weight, 108- to 120-grain competition bullets, and then on to 130- and 140-grain bullets, ideal for longer range, tactical shooting.The origin of the 6.5 Grendel may be traced back to the Soviet 7.62x39. 6.5 GrendelWith the addition of the 6.5 Grendel to the product line-up at Alexander Arms® in 2004, the history of no compromise design, engineering, and innovation continues. These ranges are far beyond those previously achievable with the AR-15 style weapon. |
- Navigate to the directory where you have saved the veeam-release package and install the package with the following commands:
For CentOS / RHEL / Oracle Linux / Fedora
For openSUSE / SLES
zypper in ./veeam-release* && zypper refresh |
For Debian / Ubuntu
yum install veeam |
Note: |
[For CentOS / RHEL] If the dkms package was installed in the OS prior to the time when you install Veeam Agent, to install the product, use the following command: yum install kmod-veeamsnap veeam. With this command, the veeamsnap kernel module will be installed from the binary kmod-veeamsnap package. Otherwise, the veeamsnap module will be installed from the source RPM package using dkms. |
zypper in veeam |
zypper in veeamsnap-kmp-default |
zypper in veeamsnap-kmp-xen |
Install Virtualbox On Centos 7 Minimal
apt-get install veeam |
- Packman repository (for openSUSE). To learn more, see Installing dkms in openSUSE.
For SLES, the dkms package is not available in the Packman repository. You must use the package intended for openSUSE. To learn more, see this Veeam KB article.
- Extended kernels, such as kernel-pae, kernel-uek and other, require appropriate kernel-devel packages to be installed, for example, kernel-pae-devel, kernel-uek-devel, and so on.
Version of the kernel-devel package must match your current kernel version. To check your current kernel version, run the uname -r command.
[For RHEL and derivatives] If the yum package manager installs packages that do not match your current kernel version, you should either update your system or fetch older versions of the required packages from the CentOS Vault repository.

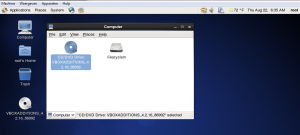
Problem: nothing provides kernel-devel needed by dkms-2.2.0.3-14.1.noarch |
root@localhost:~> rpm -qa | grep kernel-default |
- Make sure that you have allowed unsupported modules. To learn more, see this SUSE webpage.
- 08 Oct 2018: Post was created (diff)
- 28 Feb 2019: Add missing step: register peer on server (diff)
- 28 Feb 2019: Big overhaul for improved clarity (diff)
- 29 Apr 2019: Fix invalid argument to firewall-cmd (diff)
Introduction
I'm tired of OpenVPN quirks and configuration issues across my devices.Additionally, I've been planning to try out WireGuard for some time now, afterhearing praises from some different people along my way.
I set up a new CentOS box to act as the VPN server, and the client in myguide is, as usual, running Arch Linux.
The section headers below tells you whether the work is on the CentOS server(server) or the Arch Linux client (client).
Server
This host is running CentOS
The installation steps are based on https://www.wireguard.com/install/ andmay have been updated since time of writing this post.
Add the EPEL (Extra Packages for Enterprise Linux) RPM repo andinstall WireGuard and utilities
Create an empty server config file with proper permissions
Configure the wireguard network interface. Here we are using the output of wg genkey directly. The PrivateKey option in the wg-quick configuration file also accepts a file path to a file containing the private key, if that should be more desirable.
Save configuration to a file Hp dc7800 pci serial port driver windows 10.
Take note of the public key of the server. All of the clients will need it in order toestablish a wireguard connection to this server.
Client
This example client host is running Arch Linux. If you are running CentOS on your client too, repeat the installation steps as described in the previous step instead.
Install wireguard packages.
Create a folder only accessible by root and generate a private key
The contents of private.key will now look something like this:
This is a private key, hence, a secret that should not be shared with anyone.In contrast to the public key which is not considered secret and can evenbe sent over an unencrypted channel.
The public key has to be registered on the server in a later step. Take note of howto extract it:
Create a wg-quick configuration file which makes it easier to bring up anddown one or more WireGuard interfaces
Install Virtualbox 6.1 On Centos 7
- Remove IPv6 configuration if you're not using it.
- Replace the
Addresswith the IP address intended for this client, and theprefix for the subnet it belongs to. - Replace the value of
PrivateKeywith the contents of the client private.key file. - Replace the value of
PublicKeywith the public key of the server that wasdetermined in a previous section. - Replace the
Endpointwith the public IP or hostname of the server.
Server firewall configuration
If you're not running firewalld, this step may be skipped.
Create a new firewalld service definition for WireGuard
Enable the custom WireGuard service in firewalld
Enable masquerading
Reload firewalld and take a look at the zone configuration
Enable IPv4 forwarding, and, if applicable, IPv6 forwarding as well.
Make sysctl settings persistent across reboots

Problem: nothing provides kernel-devel needed by dkms-2.2.0.3-14.1.noarch |
root@localhost:~> rpm -qa | grep kernel-default |
- Make sure that you have allowed unsupported modules. To learn more, see this SUSE webpage.
- 08 Oct 2018: Post was created (diff)
- 28 Feb 2019: Add missing step: register peer on server (diff)
- 28 Feb 2019: Big overhaul for improved clarity (diff)
- 29 Apr 2019: Fix invalid argument to firewall-cmd (diff)
Introduction
I'm tired of OpenVPN quirks and configuration issues across my devices.Additionally, I've been planning to try out WireGuard for some time now, afterhearing praises from some different people along my way.
I set up a new CentOS box to act as the VPN server, and the client in myguide is, as usual, running Arch Linux.
The section headers below tells you whether the work is on the CentOS server(server) or the Arch Linux client (client).
Server
This host is running CentOS
The installation steps are based on https://www.wireguard.com/install/ andmay have been updated since time of writing this post.
Add the EPEL (Extra Packages for Enterprise Linux) RPM repo andinstall WireGuard and utilities
Create an empty server config file with proper permissions
Configure the wireguard network interface. Here we are using the output of wg genkey directly. The PrivateKey option in the wg-quick configuration file also accepts a file path to a file containing the private key, if that should be more desirable.
Save configuration to a file Hp dc7800 pci serial port driver windows 10.
Take note of the public key of the server. All of the clients will need it in order toestablish a wireguard connection to this server.
Client
This example client host is running Arch Linux. If you are running CentOS on your client too, repeat the installation steps as described in the previous step instead.
Install wireguard packages.
Create a folder only accessible by root and generate a private key
The contents of private.key will now look something like this:
This is a private key, hence, a secret that should not be shared with anyone.In contrast to the public key which is not considered secret and can evenbe sent over an unencrypted channel.
The public key has to be registered on the server in a later step. Take note of howto extract it:
Create a wg-quick configuration file which makes it easier to bring up anddown one or more WireGuard interfaces
Install Virtualbox 6.1 On Centos 7
- Remove IPv6 configuration if you're not using it.
- Replace the
Addresswith the IP address intended for this client, and theprefix for the subnet it belongs to. - Replace the value of
PrivateKeywith the contents of the client private.key file. - Replace the value of
PublicKeywith the public key of the server that wasdetermined in a previous section. - Replace the
Endpointwith the public IP or hostname of the server.
Server firewall configuration
If you're not running firewalld, this step may be skipped.
Create a new firewalld service definition for WireGuard
Enable the custom WireGuard service in firewalld
Enable masquerading
Reload firewalld and take a look at the zone configuration
Enable IPv4 forwarding, and, if applicable, IPv6 forwarding as well.
Make sysctl settings persistent across reboots
Installing Dkms On Centos 7 Command
Start the wireguard client process on the server
Letting VPN clients connect to each other (optional)
Add wireguard interface to the internal firewalld zone
Enable masquerading
Enable the services you'd like to be available on this network using firewall-cmd --zone=internal --add-service [name]. Remember to add the flag --permanent when it works. So easy to forget.
Server - Allow client to connect
Now, back in the server configuration file, add the client public key and the IP's it should be allowed to register with on the server.Copy the public key from the client and paste it into the server configuration, like below.
Restart the server. No errors should be thrown.
Client - Attempt to connect to server
Attempt to connect to the server
See if you are able to send and receive traffic, and at the same time checkyour IP address
Complete configuration
Server
Client
References
Install Virtualbox On Centos 7 Server
- https://www.wireguard.com/install/
- https://fedoraproject.org/wiki/EPEL/FAQ
- https://git.zx2c4.com/WireGuard/about/src/tools/man/wg-quick.8
- https://serverfault.com/questions/664576/should-iptables-be-this-long-many-chains
- https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-using-firewalld-on-centos-7
- https://www.ripe.net/participate/member-support/lir-basics/ipv6_reference_card.pdf